Introduction
Poker apps handle real money, identity data, and high-frequency transactions, making user data protection and financial security in poker game apps far more critical than in standard mobile applications. These platforms frequently attract credential-stuffing bots, payout fraud attempts, and account takeovers. As a result, security must safeguard not only user logins but also sensitive information and money movement. This article explains the practical controls used to secure poker apps, why they matter, and how teams implement them in real production environments.
1. Importance of Data Security in Online Poker
A poker app does not only store usernames and passwords. Instead, it often stores or processes:
- PII: email, phone, address, device identifiers, IP history, and sometimes KYC documents
- Wallet and transaction data: deposits, withdrawals, balances, payout methods, and reconciliation logs
- Gameplay data: table events, hand history, player actions, and anti-fraud signals (multi-account patterns, unusual win rates)
- Operations data: admin actions, support notes, manual adjustments, and audit logs
If attackers access this data, they can take over accounts, misuse balances, or tamper with payouts. With money involved, small gaps cause real losses and trust damage.
Abuse here is also more aggressive and more varied than in most apps, so security needs stricter controls.
2. Implementing Multi-Factor Authentication (MFA)
MFA reduces account takeover risk, but it matters most when used as step-up verification for risky actions, not only at login.
Where MFA matters most
Use MFA for high-risk actions, such as:
- withdrawals and payout method changes
- email, phone, and password changes
- new device sign-ins
- suspicious logins based on signals like repeated failures, new country/IP ranges, VPN/TOR, or “new device + withdrawal attempt”
How to implement MFA safely
- Prefer TOTP apps or push-based MFA where possible.
- If you use SMS OTP, add strict rate limits and basic abuse checks.
- Limit OTP retries and temporarily lock challenges after repeated failures.
- Keep OTP expiry short and reject reused OTPs.
- Rotate sessions after MFA success, so older tokens are not useful if leaked.
MFA is stronger when session handling is tight. So, use short-lived access tokens, rotate refresh tokens, and invalidate sessions after sensitive account changes. If you also want the broader backend picture, use this guide on scalable backend architectures for poker game apps.
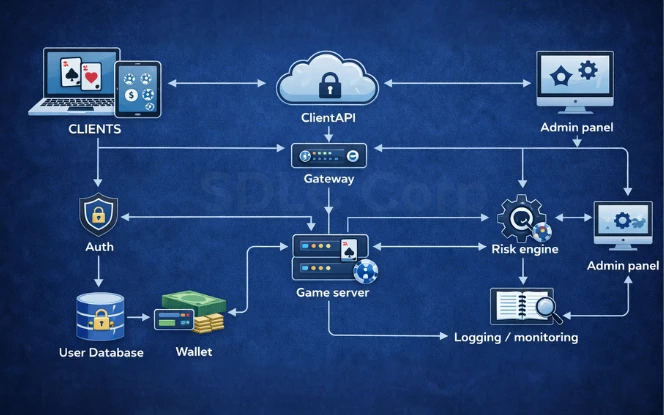
3. Security Architecture Map
Shows how poker app data flows across client, APIs, wallet, game services, and admin tools, along with the controls that protect each layer.
4. Secure Payment Processing
Payments and withdrawals carry the highest risk in poker apps. So, the goal is to reduce exposure and make fraud harder to scale.
Reduce PCI scope with tokenization
Do not store raw card data in your systems. Instead:
- use a payment gateway that returns tokens
- store only token references and transaction IDs
- keep card handling inside PCI-compliant providers
Protect payment webhooks and callbacks
Payment status often comes through webhooks. These endpoints often get targeted for replay and double-processing attempts. So:
- verify webhook signatures and reject unsigned calls
- use idempotency keys so the same event does not get processed twice
- validate state transitions (avoid impossible status jumps)
- log every state change with a trace ID for reconciliation and disputes
Secure withdrawals with step-up controls
Withdrawals attract fraud, so add:
- step-up verification on payout changes and withdrawals
- velocity limits for new accounts and first-time withdrawals
- risk checks for unusual device, location, and payout behavior
If you handle wallet events at scale, database choices also matter. So, review your storage approach using how to choose the right database for your poker game app.
5. Regular Security Audits and Vulnerability Assessments
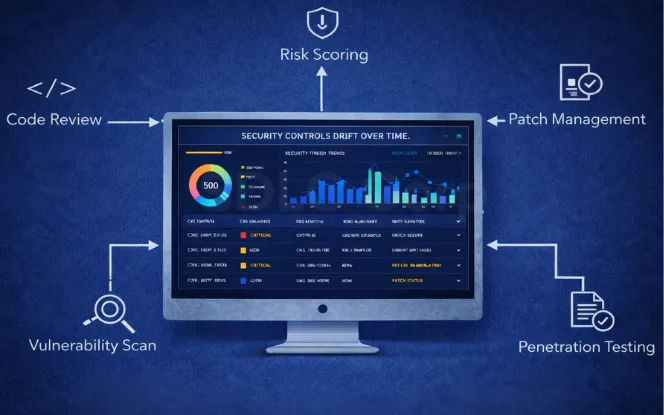
Security controls drift over time. Fast releases, new dependencies, and config changes can introduce weak points. So, audits need to be scheduled, repeatable, and tied to fixes.
What “audit” should cover in practice
A useful audit usually includes:
- Application security review: auth, access control, sessions, API validation, business logic around wallet/bonus flows
- Dependency checks: vulnerable libraries, outdated SDKs, risky transitive packages
- Infrastructure review: storage permissions, network rules, secrets handling, admin access paths
- Penetration testing: focused testing of login, wallet, withdrawals, bonus abuse paths, and admin actions
Also, run automated checks continuously, such as:
- SAST for risky code patterns
- DAST for runtime behavior and exposed endpoints
- container/image scanning for known CVEs
Most importantly, track fixes with owners and deadlines. Otherwise, audits become documentation instead of risk reduction.
6. User Education and Awareness
Even strong platforms still see phishing and reused passwords. So, user education should support technical controls without adding friction everywhere.
Practical steps that help:
- show “new login” alerts with device and location details
- warn users when they set weak or commonly reused passwords
- explain common scam patterns around withdrawals and support impersonation
- provide a clear recovery path with identity checks and cooldowns after sensitive changes
Also, keep support workflows secure. For example, avoid letting support agents change payout details without verification steps, approvals, and full logging.
7. Secure Server Infrastructure
A secure app can still leak data through weak infrastructure. So, infrastructure security should be treated as a product requirement.
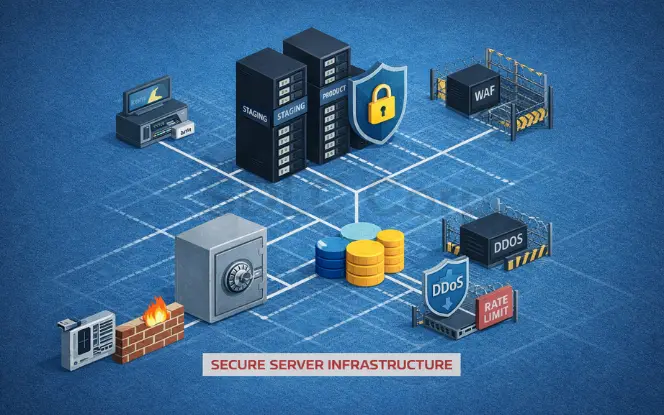
Infrastructure controls that matter
- Separate staging and production environments.
- Restrict production access through least-privilege roles.
- Store secrets in a secrets manager, not in code or shared config files.
- Encrypt storage volumes and sensitive fields using managed keys.
- Keep audit logs for privileged actions and admin access.
Network and edge protection
Poker apps face abusive traffic and automated attacks. So:
- use a WAF for common attacks
- enable DDoS protection at the edge
- rate-limit login, OTP, and wallet endpoints
- block abusive patterns like credential-stuffing bursts and OTP floods
If you want a practical operations view, read how to manage load balancing and server management for poker game apps.
Also, encryption is not only “turn on HTTPS.” Strong key management and secure service-to-service transport defaults matter as well. For a focused guide, use how to implement end-to-end encryption in poker apps.
8. Incident Response and Management
Incidents can still happen. A clear response plan helps reduce impact and speeds up recovery.
A practical incident response plan covers:
- how to revoke sessions and rotate tokens quickly
- how to rotate encryption keys when required
- how to isolate affected services or pause withdrawals temporarily
- how to preserve logs and evidence for investigation
- how to communicate with users when required
Tabletop exercises also help teams respond with fewer mistakes under pressure.
9. Compliance with Regulatory Standards
Compliance supports trust, but it does not replace security. It works better when used as a way to enforce consistent controls.
Poker apps commonly align with:
- PCI DSS for payment handling scope
- GDPR-style privacy rules for personal data handling
- KYC/AML requirements where real-money play applies
Privacy and user-data handling need retention rules, access logs, consent flows, and secure deletion. So, keep that topic separate from general security and use this focused guide on player data handling and privacy controls in poker apps.
10. Real-World Case Study: PokerStars + MOVEit Breach

What happened
- PokerStars’ U.S. entity reported unauthorized file copying during May 30–31, 2023
- The breach was discovered on June 2, 2023
- Exposed data (per public breach filings) included names and Social Security numbers
Why it happened
- The entry point was a vulnerability in MOVEit Transfer, a managed file transfer tool widely exploited in 2023
- The core issue was SQL injection (CVE-2023-34362)
- The flaw allowed unauthenticated access to MOVEit’s database and stored data
How it happened (simple technical chain)
- A MOVEit server exposed to the internet contained the vulnerable endpoint
- The attacker used SQL injection to reach database-backed access paths
- Files available through transfer workflows were copied and exfiltrated
- This pattern matched the broader MOVEit exploitation wave
What a B2B Buyer Should Take From It
- The highest-risk data often sits outside core game servers
- File transfers, exports, support tooling, and compliance workflows frequently hold the most sensitive data
- “We don’t store card data” is not a complete security story
- Identity data (KYC / SSN where applicable) can still trigger fraud and regulatory exposure
- Buyers should ask vendors for proof, not claims, including:
- Patch cadence for third-party tools
- Network segmentation evidence
- Export and access logging
- Incident drill results
- Patch cadence for third-party tools
Solutions (Technical — Key Points Only)
- Isolate transfer tools: place MFT systems in segmented zones with strict allowlists
- Patch and validate exposure fast: inventory internet-facing services and apply critical CVE fixes immediately
- Rotate secrets after containment: rotate API keys, SFTP credentials, database passwords, and integration tokens
- Treat exports like withdrawals: require step-up verification, strict role approvals, and anomaly alerts
- Minimize exported data: export only required fields; tokenize identifiers; avoid full sensitive IDs unless mandated
- Make logs investigation-ready: use immutable audit logs showing who exported what, when, and from where
- Vendor-risk SLAs: require patch SLAs, breach notification SLAs, and monitoring evidence for tools touching PII
11. Security Controls and Evidence Buyers Should Expect
This table shows key security controls, the evidence buyers should request, and how each control is measured and owned.
| Security Control | Proof the buyer can ask for | KPI (measurable) | Owner |
|---|---|---|---|
| MFA on withdrawals + payout changes | MFA event logs + policy config export | ATO rate, withdrawal fraud rate | Backend |
| Token rotation after step-up | Token invalidation logs + session list | Stolen-token reuse blocked % | Backend |
| Webhook signature verification | Signed payload logs + failure alerts | Fake webhook attempts blocked | Backend |
| Wallet ledger + state machine | Ledger export + reconciliation sample | Reconciliation mismatch rate | Finance Eng |
| Admin RBAC + approvals | Role change logs + approval records | Unauthorized admin actions = 0 | Security/Ops |
| Immutable audit logs | WORM/append-only storage proof | Log tamper alerts = 0 | DevOps |
| Incident drills | Drill report + response timeline | MTTD / MTTC / MTTR | Security/Ops |
Conclusion
Poker app security is stronger when built in layers. Secure identity, payments, APIs, storage, and operations as one system. Keep audits and monitoring active because threats and configurations change over time.
If your team also wants to validate fairness signals alongside security, RNG compliance matters too. You can review RNG certification for poker software.
Quick checklist
✔️ MFA for withdrawals and key account changes
✔️ Tokenized payments with signed, idempotent webhooks
✔️ Token rotation and session invalidation on sensitive changes
✔️ Encryption in transit and at rest with tight key access
✔️ RBAC for admin and wallet actions
✔️ Alerts for login, wallet, and admin anomalies
✔️ Regular scans, audits, and pentests
✔️ Incident playbooks with periodic drills
FAQ's
What’s the highest-risk flow in a real-money poker app?
It’s the login → wallet → withdrawal path. Therefore, secure sessions, payout edits, and withdrawals more aggressively than general browsing.
Where do poker apps leak data even with encryption enabled?
Leaks often happen through admin tools, misconfigured storage, and logs. Therefore, lock RBAC, tighten storage policies, and prevent PII from entering logs.
Where should MFA be mandatory in a poker app?
Enforce MFA on withdrawals, payout method changes, and new device sign-ins. Additionally, rotate sessions after MFA so stolen tokens stop working.
What’s the most common OTP weakness attackers exploit?
Teams skip abuse controls. Therefore, apply rate limits, short expiry, retry caps, and lockouts tied to device/IP risk.
How do payout fraud attacks work without breaking the payment gateway?
Attackers take over accounts, change payout details, then withdraw fast. Therefore, use step-up verification, velocity limits, and risk checks before payouts.
What should security audits test first for poker apps?
Start with wallet endpoints, admin actions, password reset, and device change flows. Therefore, testing targets the highest-loss areas, not low-impact UI issues.




